The philosophy of Elves in Linux threat detection
Introduction
Software is code. Code that is intricately linked and packaged into an executable program through esoteric ABI specs that few understand; an arcane art that few have been initiated into, and even less of whom are masters of. Take for example, the ELF binary format. The most widely used binary format in existence running on servers, IOT devices, and phone. The ELF binary format (The standard UNIX/Linux format since 1995) supports core files, executables, shared libraries, and relocatable code. It is used for firmware, kernel, and userland programs. All code that is linked, shared, executed, and debugged in Linux are done so with ELF linkers, loaders, and debuggers.
Where within this complex chain of linking, loading, execution and debugging should we be concerned about APT's (Advanced presistent threats)? The answer is Everywhere!
The integrity of the code being executed should be under heavy question. Software attestation such as NetBSD's Veriexec, and Linux IMA (Integrity measurement architecture) are valiant efforts but not full proof and subject to their own vulnerabilities.
Advanced Persistent Threats and ELF
The very nature of Advanced persistent threats is that they are both Persistent and "Advanced". State of the art technology that gives hackers a stealth and persistent presence on a compromised system. Rootkits and backdoors of this nature will go completely undetected on your system no matter the price you pay for your CrowdStrike Falcon license.
The following video illustrates a Linux anti-forensics technique for execution using thread injection to load an ELF executable into an existing process image. In essence this allows a program to run entirely within the address space of another and will not show up in 'ps', and will fail to be detected by other approaches which assume a kernel rootkit is responsible for hiding the process.
Saruman anti-forensics injector
In this video Linux CrowdStrike Falcon is running in Aggressive mode. It's strengths do not involve advanced forensics of process memory and it therefore fails to detect a hidden remote backdoor.
APT's cannot be classified as Malware. Malware such as botnets and other malicious programs have nothing stealth about them (generally speaking). But an APT by definition is advanced technology for concealing a presence and can therefore be used as a contraceptive harness for hiding other software. Often existing only in memory or within the Shadows of the complex ELF executable structure. APT's are Advanced, cutting edge, and therefore elusive.
In particular, the ELF format is compelling for Hackers, Rootkit authors, and Virus enthusiasts. It is flexible and used throughout the entire runtime eco-system from the ELF firmware loader and up. The attack surface is rich and a rather expansive playground for APT's.
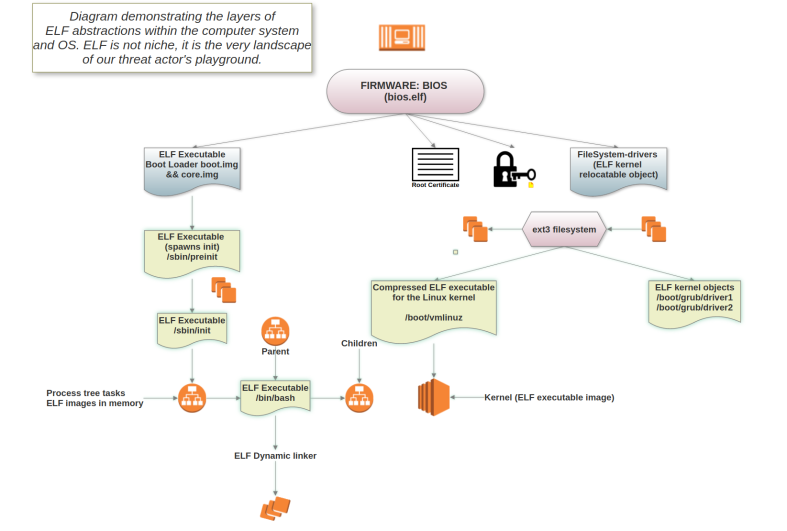
Your computer is constantly jumping from one ELF to the next... whether it be in protected mode, ring-0, or during bootup; an ELF is always near.
A history of ELF infection
The original adepts: Silvio Cesare, Mayhem and the Grugq -- these guys, for better or for worse, knew the power within executable linking concepts and wrote the original code and papers on ELF Virus infection [1], Sophisticated ELF backdoors [2], and very new data contraception techniques [3]. These new papers were revolutionary and considered very elite and esoteric doctrines on parasitic code infections within ELF. We saw radical implementations of ELF kernel module injection via /dev/kmem [4], dynamic linking subversion [5], and userland-exec's [6] come into the scene with new terminology such as "anti-forensics" and "process-infection".
The scene was vibrant and new. Treasures were still being newly discovered and exploited, and all of the security innovation in the 90's was being generated by the underground scene. In particular, ELF became a focus of a few elite who pioneered the original thoughts on ELF infection.
Over the last two decades the ELF binary format specification is essentially the same but there has been an evolution to the mechanics of linking and loading with the advent of PIE executable's, RELRO, strict-linking, fcf-protection, separate-code, and more... The ELF landscape for infection is constantly expanding, and varies between Operating systems.
On a more recent note, there is a published paper in tmp.0ut by ElfMaster [7] that illustrates writing a custom dynamic linker from scratch which can load ELF relocatable objects into memory at runtime that serve as sophisticated APT's: rootkits, viruses, backdoors. This technique has not been observed in the wild by anyone that I know, but serves as an extremely powerful technique that isn't so trivial to detect.
Open Sourcing "Arcana ElfScan" for binary infection detection
At Arcana technologies we have deep insight through 17+ years of experience in ELF Viruses, implants, and backdoors that surreptitiously reside within ELF binaries, process memory and kernel memory. This has led to multiple technologies that have been created over the years for process memory analysis, binary analysis and kernel memory analysis in Linux.
With the advent of this blog-post we are open sourcing a powerful ELF binary scanning technology Arcana ElfScan This source code has been open sourced under the MIT license.
Arcana ElfScan was originally invented in 2018. It is capable of detecting many ELF infections commonly used by ELF Virus technology for APT (Advanced persistent threats): ELF binary backdoors, userland rootkits and virus infections. See Arcana About for more details on Arcana's infection analysis capabilities.
Currently Arcana's ElfScan technology officially supports scanning x86_32/x86_64 ELF executables. Arcana is powered by an intelligent heuristics engine with libelfmaster under the hood for ELF parsing and forensic reconstruction of ELF sections headers, symbols, and other meta-data. Arcana offers a plugin system as well that allow developers to enhance the software without modifying the code base directly.
Our goal is to provide the Security and Linux threat detection community with an open source solution that is capable of detecting serious threats, while continuing to enhance the security and proficiency of the technology through an open source community.
If you are interested in contributing to Arcana, submit a PR to the github [8] with your patch and it will be reviewed by one of our developers.
Contact
elfmaster [at] arcana-technologies.io
